About Us
Cyber technology has become pervasive and indispensable. As cyber technology advances and the Internet of Everything becomes reality, it is critical that these systems are secure and that they operate for the benefit of humankind.
Research Areas
Automatically reverse engineer and transform binaries
Retrofit legacy binaries with security
Break the software monoculture
Automatically find weakness in real-world binaries
Malware analysis at scale
Featured Publications
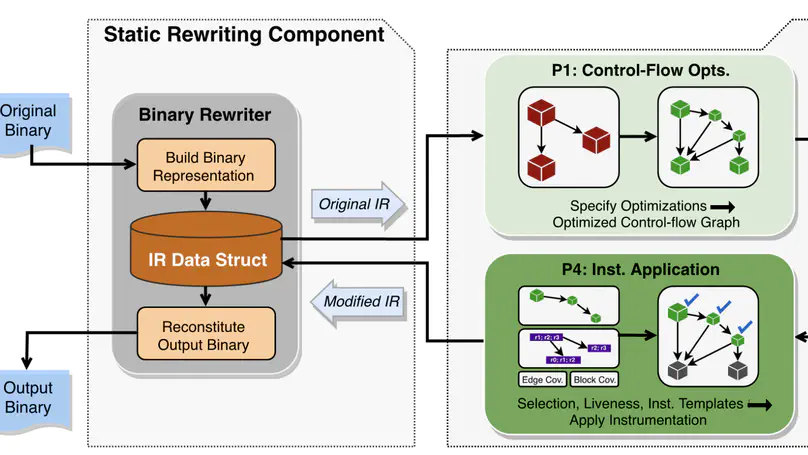
We demonstrate how to achieve fuzzing performance for binary programs that is on par with compiler-based fuzzing approaches.

This paper tackles the challenges of adapting coverage-guided tracing to fuzzing’s most ubiquitous coverage metrics. We introduce and implement a suite of enhancements that expand CGT’s introspection to fuzzing’s most common code coverage metrics, while maintaining its orders-of-magnitude speedup over conventional always-on coverage tracing. We evaluate their trade-offs with respect to fuzzing performance and effectiveness across 12 diverse real-world binaries (8 open- and 4 closed-source). On average, our coverage-preserving CGT attains near-identical speed to the present block-coverage-only CGT, UnTracer; and outperforms leading binary- and source-level coverage tracers QEMU, Dyninst, RetroWrite, and AFL-Clang by 2–24x, finding more bugs in less time.

Malware written in dynamic languages such as PHP routinely employ anti-analysis techniques such as obfuscation schemes and evasive tricks to avoid detection. This paper presents a system called Cubismo to solve this pressing problem. It processes potentially malicious files and decloaks their obfuscations, exposing the hidden malicious code into multiple files. Cubismo achieves improved detection by exploring all executable statements of a suspect program counterfactually to see through complicated polymorphism, metamorphism and, obfuscation techniques and expose any malware. Cubismo is highly effective in dissecting sophisticated metamorphic malware with multiple layers of obfuscation. Cubismo enables VirusTotal to detect 53 out of 56 zero-day malware samples in the wild, which were previously undetectable.







